- uint32_t pKeyAES[4] = {0xFEFFE992,0x8665731C,0x6D6A8F94,0x67308308};
- uint32_t pInitVectAES[4] = {0xCAFEBABE,0xFACEDBAD,0xDECAF888,0x00000002};
- __ALIGN_BEGIN static const uint32_t HeaderAES[5] __ALIGN_END = {
- 0xfeedface,0xdeadbeef,0xfeedface,0xdeadbeef,0xabaddad2};
- uint32_t Plaintext[PLAINTEXT_SIZE] = {0xd9313225,0xf88406e5,0xa55909c5,0xaff5269a,
- 0x86a7a953,0x1534f7da,0x2e4c303d,0x8a318a72,
- 0x1c3c0c95,0x95680953,0x2fcf0e24,0x49a6b525,
- 0xb16aedf5,0xaa0de657,0xba637b39};
- uint32_t Ciphertext[15] = {0x42831ec2,0x21777424,0x4b7221b7,0x84d0d49c,
- 0xe3aa212f,0x2c02a4e0,0x35c17e23,0x29aca12e,
- 0x21d514b2,0x5466931c,0x7d8f6a5a,0xac84aa05,
- 0x1ba30b39,0x6a0aac97,0x3d58e091};
- uint32_t ExpectedTAG[4]={0x5bc94fbc,0x3221a5db,0x94fae95a,0xe7121a47};
pInitVectAES:IV Initialization vector
HeaderAES:附加认证数据(AAD)
Plaintext:明文
Ciphertext:期望密文
ExpectedTAG:期望TAG(消息认证码)
2、Show_Message(void)
- static void Show_Message(void)
- {
- printf("板子名称:%s\r\n",BSP_GetBoardName());
- printf("版本:%d\r\n",BSP_GetVersion());
- printf("板子ID:%s\r\n",BSP_GetBoardID());
- printf("[STM32 Nucleo-64测评] 4、AES加密GCM模式测试\r\n");
-
- }
3、main()片段
- Show_Message();
-
- /* USER CODE BEGIN 2 */
- /*##-2- Encryption Phase #################################################*/
-
- printf("\r\nEncryption Phase #################################################\r\n");
- printf("HAL_CRYP_Encrypt start...[uwTick=%d]\r\n",uwTick);
- if (HAL_CRYP_Encrypt(&hcryp, Plaintext, PLAINTEXT_SIZE, EncryptedText, TIMEOUT_VALUE) != HAL_OK)
- {
- /* Processing Error */
- Error_Handler();
- }
- printf("HAL_CRYP_Encrypt finished...[uwTick=%d]\r\n",uwTick);
- /*Compare results with expected buffer*/
-
- printf("加密结果:\r\n");
- for(int i=0;i<PLAINTEXT_SIZE;i++){
- printf("0x%08X,",EncryptedText[i]);
- }
- printf("\r\n");
-
-
- printf("预期加密结果:\r\n");
- for(int i=0;i<PLAINTEXT_SIZE;i++){
- printf("0x%08X,",Ciphertext[i]);
- }
- printf("\r\n");
- if(memcmp(EncryptedText, Ciphertext, 4*PLAINTEXT_SIZE) != 0)
- {
- /* Processing Error */
- Error_Handler();
- }
- /* Compute the authentication TAG */
- if (HAL_CRYPEx_AESGCM_GenerateAuthTAG(&hcryp,TAG, TIMEOUT_VALUE) != HAL_OK)
- {
- /* Processing Error */
- Error_Handler();
- }
-
- printf("加密令牌TAG结果:\r\n");
- for(int i=0;i<4;i++){
- printf("0x%08X,",TAG[i]);
- }
- printf("\r\n");
- /*Compare results with expected buffer*/
- if(memcmp(TAG, ExpectedTAG, 16) != 0)
- {
- /* Processing Error */
- Error_Handler();
- }
- printf("预期加密令牌TAG结果:\r\n");
- for(int i=0;i<4;i++){
- printf("0x%08X,",ExpectedTAG[i]);
- }
- printf("\r\n");
-
- /*##-3- Decryption Phase #################################################*/
- printf("\r\n\Decryption Phase #################################################\r\n");
- printf("HAL_CRYP_Decrypt start...[uwTick=%d]\r\n",uwTick);
- if (HAL_CRYP_Decrypt(&hcryp,Ciphertext , PLAINTEXT_SIZE, DecryptedText, TIMEOUT_VALUE) != HAL_OK)
- {
- /* Processing Error */
- Error_Handler();
- }
- printf("HAL_CRYP_Decrypt finished...[uwTick=%d]\r\n",uwTick);
-
- printf("解密结果:\r\n");
- for(int i=0;i<PLAINTEXT_SIZE;i++){
- printf("0x%08X,",DecryptedText[i]);
- }
- printf("\r\n");
-
- /*Compare results with expected buffer*/
- if(memcmp(DecryptedText, Plaintext, 16) != 0)
- {
- /* Processing Error */
- Error_Handler();
- }
- printf("明文:\r\n");
- for(int i=0;i<PLAINTEXT_SIZE;i++){
- printf("0x%08X,",Plaintext[i]);
- }
- printf("\r\n");
- /* Compute the authentication TAG */
- if (HAL_CRYPEx_AESGCM_GenerateAuthTAG(&hcryp,TAG, TIMEOUT_VALUE) != HAL_OK)
- {
- /* Processing Error */
- Error_Handler();
- }
-
- printf("解密令牌TAG结果:\r\n");
- for(int i=0;i<4;i++){
- printf("0x%08X,",TAG[i]);
- }
- printf("\r\n");
- /*Compare results with expected buffer*/
- if(memcmp(TAG, ExpectedTAG, 16) != 0)
- {
- /* Processing Error */
- Error_Handler();
- }
- printf("预期解密令牌TAG结果:\r\n");
- for(int i=0;i<4;i++){
- printf("0x%08X,",ExpectedTAG[i]);
- }
- printf("\r\n");
HAL_CRYP_Decrypt是解密函数
HAL_CRYPEx_AESGCM_GenerateAuthTAG生成TAG
4、AES初始化
- static void MX_AES_Init(void)
- {
- /* USER CODE BEGIN AES_Init 0 */
- /* USER CODE END AES_Init 0 */
- /* USER CODE BEGIN AES_Init 1 */
- /* USER CODE END AES_Init 1 */
- hcryp.Instance = AES;
- hcryp.Init.DataType = CRYP_NO_SWAP;
- hcryp.Init.KeySize = CRYP_KEYSIZE_128B;
- hcryp.Init.pKey = (uint32_t *)pKeyAES;
- hcryp.Init.pInitVect = (uint32_t *)pInitVectAES;
- hcryp.Init.Algorithm = CRYP_AES_GCM_GMAC;
- hcryp.Init.Header = (uint32_t *)HeaderAES;
- hcryp.Init.HeaderSize = 5;
- hcryp.Init.DataWidthUnit = CRYP_DATAWIDTHUNIT_WORD;
- hcryp.Init.HeaderWidthUnit = CRYP_HEADERWIDTHUNIT_WORD;
- hcryp.Init.KeyIVConfigSkip = CRYP_KEYIVCONFIG_ALWAYS;
- hcryp.Init.KeyMode = CRYP_KEYMODE_NORMAL;
- if (HAL_CRYP_Init(&hcryp) != HAL_OK)
- {
- Error_Handler();
- }
- /* USER CODE BEGIN AES_Init 2 */
- /* USER CODE END AES_Init 2 */
- }
五、运行效果
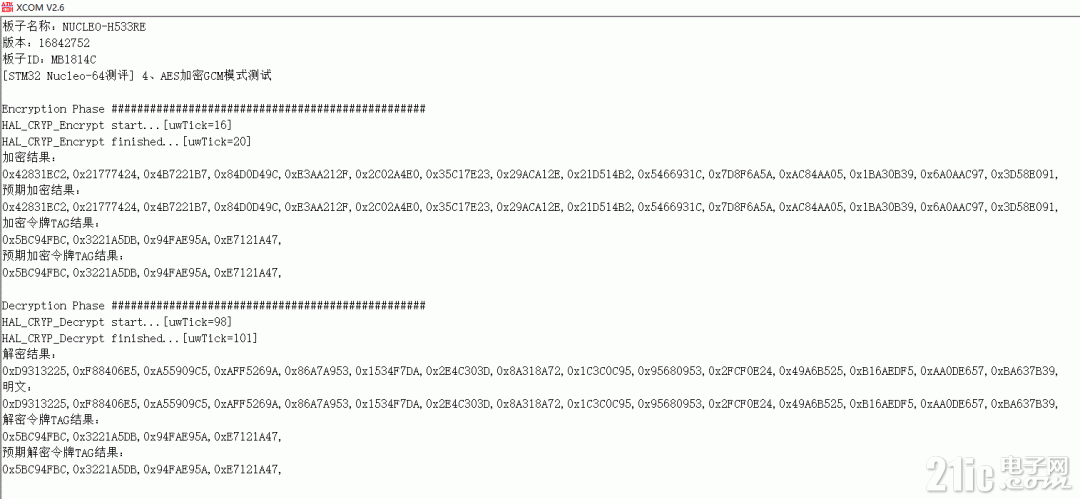
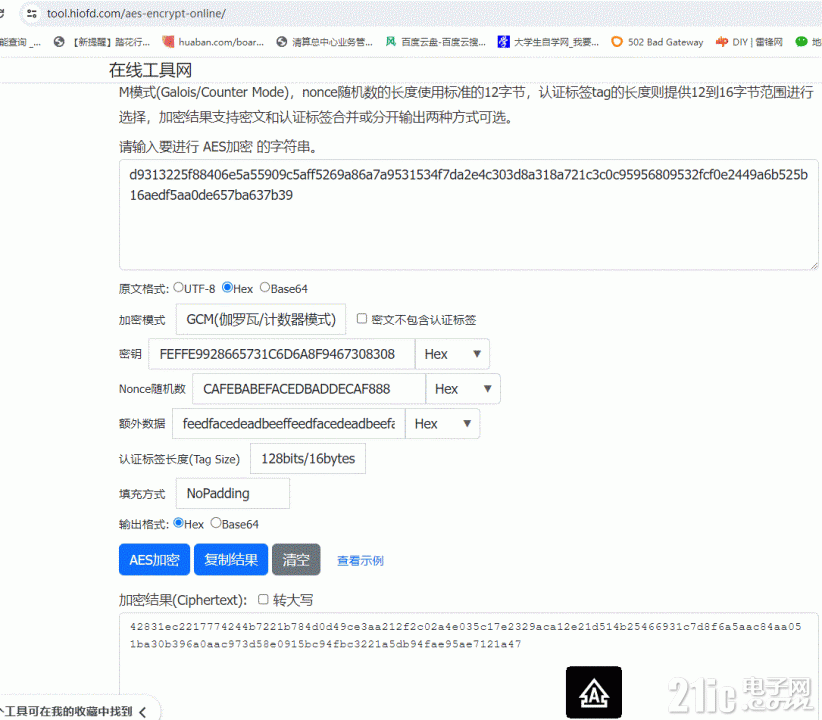
网上AES在线工具计算比较:
六、总结
1、加密解密结果正确。
2、加密和解密耗时大约3、4个TICKS。
3、官方例子位置:STM32Cube_FW_H5_V1.3.0\Projects\NUCLEO-H533RE\Examples\CRYP\CRYP_AES_GCM_Padding